Introduction to SPF, DKIM, and Email Authentication
Exploring SPF, DKIM, and DMARC
Email security is fundamental to digital communication, especially for domain owners and businesses.
SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) are essential components in this security framework.
SPF: It helps in authenticating the sender's IP addresses, reducing the risk of email spoofing. By defining SPF records in DNS, domain owners can specify which mail servers are authorized to send emails on their behalf.
DKIM: This adds a digital signature to all email message headers, ensuring the same email message's content remains unchanged from sender to recipient. DKIM uses a pair of keys (private and public) to implement this security measure.
DMARC: It combines the features of SPF and DKIM to provide a robust method for handling unauthenticated emails, thereby improving email deliverability and protecting the a domain owner's reputation.
Email Security: A Critical Concern
Email security strategies like SPF, DKIM, and DMARC are crucial for protecting against common threats such as phishing attacks. They build trust with email servers and mailbox providers, ensuring that the email sender is authenticated:
- Managing SPF Records: One of the challenges is incorporating multiple ESPs (Email Service Providers) and IP addresses in the SPF record. It's vital to include all legitimate sending sources to prevent authentic emails from being wrongly marked as spam.
- Setting Up DKIM: Configuring DKIM involves detailed steps, like setting DNS txt records and aligning DKIM signatures correctly with the domain's DNS records.
- Implementing DMARC: This requires setting a policy in the domain's DNS settings, guiding how receiving servers should handle emails that fail SPF or DKIM checks.
Each of these protocols plays a distinct role in safeguarding email communications, and their effective implementation can significantly enhance a domain's email security posture.
Understanding SPF Record (Sender Policy Framework) in Depth
Decoding SPF: Domain Owners' Tool for Email Verification
SPF, a cornerstone in email and authentication protocols, empowers domain and email account owners to safeguard their email communication.
This protocol is key in verifying that emails originate from authorized mail servers, significantly mitigating the risk of domain spoofing and phishing attacks.
- Function: SPF validates outgoing email messages made from your domain, checking against a list of approved IP addresses.
- Mechanism: It cross-references the sender's IP address with the domain's SPF record in your domain's DNS settings.
- Benefit: Successfully validated emails are less likely to end up in the next recipient's inbox or spam folder, enhancing email deliverability.
SPF Records: Creation and Management
Creating and managing an SPF record is a detailed process that requires careful attention:
- List Authorized Sending Sources: Include all mail servers and ESPs authorized to send emails on your domain's behalf.
- Craft the SPF Record: This TXT record in your DNS system should accurately reflect all authorized sources.
- Update and Maintain: Regularly revise the SPF record to reflect any changes in your email server infrastructure.
IP Addresses in SPF: Significance and Management
IP addresses play a pivotal role in the SPF framework:
- Authorized IPs: Ensure that the SPF record includes all legitimate authorized IP addresses. This prevents unauthorized use of your domain.
- Dynamic Nature: As your email infrastructure evolves, updating the existing SPF record along with new IP addresses is crucial.
What Happens If I Don't Have (Correct) SPF Record?
How do SPF records impact your business?
Lacking a correct SPF record has far-reaching consequences, touching various facets of email communication and domain integrity:
- Compromised Email Deliverability: Your legitimate email risks being classified as spam without a proper SPF record. This is especially detrimental for businesses relying on email marketing campaigns or cold outreach for lead generation. The direct impact? Potential leads never see your emails, leading to a notable decrease in engagement and sales opportunities.
- Marketing Campaign Setbacks: When marketing emails consistently land in spam folders, the effectiveness of these campaigns diminishes. This can lead to a significant drop in return on investment (ROI), as the reach and engagement with potential customers are severely hindered.
- Disrupted User Engagement: For services like SaaS tools, essential communications such as verification emails or transactional notifications might not reach the user’s inbox. This leads to a poor user experience, potentially affecting user acquisition and retention.
- DNS TXT Record and DKIM Signature Issues: Inaccurate SPF records can disrupt the alignment with DKIM signatures, another crucial component of email authentication. This misalignment further affects trust with email servers and recipients.
- Reputation and Trust Challenges: The domain's reputation suffers as email servers start flagging your emails as potential threats. Rebuilding this trust with email service providers and recipients can be a long, challenging process.
- Operational Inefficiencies: Internal communications can be hampered if important emails are misclassified as spam. This can lead to missed deadlines, operational delays, and decreased productivity.
- Domain Provider and Email Server Strain: Incorrect SPF records can put additional strain on your domain provider and email servers, as they have to handle a higher volume of bounced emails and complaints.
In summary, maintaining an accurate SPF record is crucial for ensuring optimal email deliverability, preserving the domain's reputation, and maintaining effective communication channels. It's a key element of your overall digital presence and should be managed with attention and expertise.
Comprehensive Guide to DomainKeys Identified Mail (DKIM)
The Need for DKIM in Email Security
DomainKeys Identified Mail (DKIM) stands as a crucial line of defense in today's email security landscape. It serves as a sophisticated method for email servers and recipients to verify that an email has indeed originated from the claimed domain, a vital step in preventing email spoofing and enhancing domain security.
- Purpose: DKIM ensures the authenticity of the email sender and the integrity of the message.
- Function: It uses a digital signature, attached to the email header, which is verified using the sender's public key published in their DNS records.
- Impact: By confirming the legitimacy of the sender, DKIM significantly reduces the risk of phishing scams and spam, elevating a domain's trustworthiness in the digital realm.
Digital Signatures: The DKIM Authentication Mechanism
Digital signatures are at the heart of the DKIM process, providing a cryptographic seal of approval for each outgoing email.
- Mechanism: When sending an email, the server generates a unique DKIM signature for the message. This signature, created using a private key, is included in the email's header.
- Verification: Upon receiving the email, the recipient’s server retrieves the sender's public key from the corresponding DNS txt record. It then uses this key to verify the DKIM signature.
- Outcome: Successful verification indicates that the email has not been tampered with in transit and that the sender is indeed who they claim to be.
Crafting and Implementing DKIM Records for Mail Servers
Setting up DKIM involves several critical steps to ensure that email servers can properly generate and verify signatures:
- Generating Keys: The first step involves creating a pair of cryptographic keys – a private key for signing emails and a public key for verification.
- Publishing the Public Key: The public key is published in the domain's DNS records as a txt record. This makes it accessible for anyone needing to verify the DKIM signature.
- Configuring the Mail Server: The mail server needs to be configured to automatically sign outgoing messages using the private key.
Email Security and Business Implications
The absence or incorrect implementation of DKIM can have several repercussions:
- Email Delivery Challenges: Without DKIM, emails are more likely to be rejected or marked as spam by receiving servers, impacting email deliverability and communications efficiency.
- Compromised Reputation: Continuous email delivery issues can tarnish the domain's reputation, making it difficult for future emails to reach their intended recipients.
- Operational Risks: For businesses, especially those heavily reliant on email communication (like email service providers), DKIM issues can lead to operational disruptions and potential revenue loss.
What Happens If I Don't Have a (Correct) DKIM Record?
The absence or incorrect configuration of a DKIM (DomainKeys Identified Mail) record can have significant repercussions for your email communication and overall domain health:
- Increased Risk of Email Spoofing and Phishing Attacks: Without DKIM, it becomes easier for attackers to impersonate your domain in phishing scams. This not only endangers the recipients but also damages your domain’s credibility.
- Email Delivery Issues: Emails lacking a valid DKIM signature are more likely to be flagged as spam by email servers. This can lead to essential communications being missed by your audience, including customers, partners, and internal team members.
- Damaged Sender Reputation: Consistent delivery of emails to spam folders or outright rejections by recipient servers can degrade your domain’s reputation. This could lead to long-term deliverability challenges, as email servers become increasingly suspicious of emails from your domain.
- Operational Inefficiencies: For companies where email is a critical operational tool, DKIM issues can disrupt workflows. Important transactional emails like order confirmations, shipping notifications, or customer inquiries might not reach their intended recipients.
- Legal and Compliance Risks: Certain industries have strict regulations regarding data protection and communication security. Lack of proper DKIM records could potentially lead to compliance issues, with legal and financial ramifications.
The Need for DKIM in Email Security
DomainKeys Identified Mail (DKIM) stands as a crucial line of defense in today's email security landscape. It serves as a sophisticated method for email servers and recipients to verify that an email has indeed originated from the claimed domain, a vital step in preventing email spoofing and enhancing domain security.
- Purpose: DKIM ensures the authenticity of the email sender and the integrity of the message.
- Function: It uses a digital signature, attached to the email header, which is verified using the sender's public key published in their DNS records.
- Impact: By confirming the legitimacy of the sender, DKIM significantly reduces the risk of phishing scams and spam, elevating a domain's trustworthiness in the digital realm.
Digital Signatures: The DKIM Authentication Mechanism
Digital signatures are at the heart of the DKIM process, providing a cryptographic seal of approval for each outgoing email.
- Mechanism: When sending an email, the server generates a unique DKIM signature for the message. This signature, created using a private key, is included in the email's header.
- Verification: Upon receiving the email, the recipient’s server retrieves the sender's public key from the corresponding DNS txt record. It then uses this key to verify the DKIM signature.
- Outcome: Successful verification indicates that the email has not been tampered with in transit and that the sender is indeed who they claim to be.
Crafting and Implementing DKIM Records for Mail Servers
Setting up DKIM involves several critical steps to ensure that email servers can properly generate and verify signatures:
- Generating Keys: The first step involves creating a pair of cryptographic keys – a private key for signing emails and a public key for verification.
- Publishing the Public Key: The public key is published in the domain's DNS records as a txt record. This makes it accessible for anyone needing to verify the DKIM signature.
- Configuring the Mail Server: The mail server needs to be configured to automatically sign outgoing messages using the private key.
Email Security and Business Implications
The absence or incorrect implementation of DKIM can have several repercussions:
- Email Delivery Challenges: Without DKIM, emails are more likely to be rejected or marked as spam by receiving servers, impacting email deliverability and communications efficiency.
- Compromised Reputation: Continuous email delivery issues can tarnish the domain's reputation, making it difficult for future emails to reach their intended recipients.
- Operational Risks: For businesses, especially those heavily reliant on email communication (like email service providers), DKIM issues can lead to operational disruptions and potential revenue loss.
What Happens If I Don't Have a (Correct) DKIM Record?
The absence or incorrect configuration of a DKIM (DomainKeys Identified Mail) record can have significant repercussions for your email communication and overall domain health:
- Increased Risk of Email Spoofing and Phishing Attacks: Without DKIM, it becomes easier for attackers to impersonate your domain in phishing scams. This not only endangers the recipients but also damages your domain’s credibility.
- Email Delivery Issues: Emails lacking a valid DKIM signature are more likely to be flagged as spam by email servers. This can lead to essential communications being missed by your audience, including customers, partners, and internal team members.
- Damaged Sender Reputation: Consistent delivery of emails to spam folders or outright rejections by recipient servers can degrade your domain’s reputation. This could lead to long-term deliverability challenges, as email servers become increasingly suspicious of emails from your domain.
- Operational Inefficiencies: For companies where email is a critical operational tool, DKIM issues can disrupt workflows. Important transactional emails like order confirmations, shipping notifications, or customer inquiries might not reach their intended recipients.
- Legal and Compliance Risks: Certain industries have strict regulations regarding data protection and communication security. Lack of proper DKIM records could potentially lead to compliance issues, with legal and financial ramifications.
Exploring DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC: Bridging SPF and DKIM for Enhanced Security
DMARC stands as a robust framework, synergizing SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to fortify email security. This protocol plays a critical role in safeguarding email communication for domain owners and email service providers.
- Integration with SPF and DKIM: DMARC leverages the strengths of both SPF and DKIM, providing an additional layer of verification to ensure that an email genuinely originates from the stated domain.
- Preventing Email Spoofing: By setting clear policies on how to handle emails failing SPF or DKIM checks, DMARC significantly mitigates the risks of domain spoofing and phishing attacks.
- Enhancing Email Deliverability: Proper implementation of DMARC can improve a domain's reputation, leading to better email deliverability rates and reducing the likelihood of emails landing in the spam folder.
How DMARC Records Helps in Email Protection
Understanding the operational mechanics of DMARC records is crucial for effective email protection.
- DMARC Record Setup: DMARC policies are articulated through TXT records in the domain's DNS system. These policies instruct recipient email servers on how to handle emails that fail SPF or DKIM checks.
- Reporting Mechanism: DMARC includes a reporting feature, where recipient servers send reports back to the sender's domain. These reports provide insights into email delivery issues, aiding in quick remediation.
Domain Owners and DMARC: A Strategic Approach
For domain owners, implementing DMARC is a strategic move with several operational benefits.
- Protecting Email Servers and Recipients: By specifying DMARC policies, domain owners can dictate actions for unauthenticated messages, thus safeguarding both their email servers and their recipients.
- Compliance and Trust: In certain industries, DMARC compliance is becoming increasingly important. It not only enhances security but also builds trust with customers and partners.
- Monitoring and Adjusting Email Practices: The insights gleaned from DMARC reports enable domain owners to monitor and adjust their email authentication practices continuously. This proactive approach ensures the highest level of email security and efficiency.
What Happens If I Don't Have a (Correct) DMARC Record?
Not having a correctly configured DMARC (Domain-based Message Authentication, Reporting, and Conformance) record can have significant implications for a domain's email security and overall digital communication strategy:
- Vulnerability to Email Spoofing and Phishing: Without DMARC, your domain remains susceptible to spoofing and phishing attacks. Attackers can more easily impersonate your domain in emails, potentially harming your recipients and damaging your brand's reputation.
- Compromised Email Deliverability: DMARC aids in authenticating your emails. Without it, there's a higher risk of your legitimate emails being incorrectly flagged as spam. This can lead to important messages not reaching their intended recipients, affecting communication and business operations.
- Lack of Insight into Email Issues: One of the key features of DMARC is its reporting function. Without these reports, you lose valuable insights into how your emails are being handled by different email servers and recipients. This data is crucial for identifying and rectifying deliverability issues.
- Reduced Trust with Email Providers and Recipients: DMARC is increasingly recognized as a standard practice for email security. Not implementing it can lead to a loss of trust with email providers and recipients, who may view your domain as less secure.
- Potential Compliance Issues: In some industries, especially those handling sensitive information, DMARC compliance is becoming a standard requirement. Not having a proper DMARC record could result in non-compliance with industry standards or regulations.
Practical Scenarios: SPF and DKIM Implementation
Scenario Analysis: Establishing SPF and DKIM in Diverse Contexts
Implementing SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) is crucial for domains ranging from small businesses to large organizations. Let's delve into how these protocols are applied in different environments:
For a Growing Startup:
- Challenge: Startups often rapidly scale their email activities, necessitating robust email authentication to maintain credibility and email deliverability.
- Solution: Implement SPF to list authorized sending IPs, including cloud-based email servers. For DKIM, generate a digital signature for domain host for each email, ensuring it aligns with DNS txt records. Regularly review to include new domains or email providers.
Large Corporation with Multiple Departments:
- Challenge: A corporation with multiple departments might use various email servers and third-party email service providers.
- Solution: Consolidate SPF records to cover all authorized IP addresses. Implement DKIM with unique keys for different departments, ensuring each is correctly registered in the domain's DNS settings.
E-commerce Platforms:
- Challenge: High volume of transactional emails and newsletters.
- Solution: Robust SPF and DKIM configurations to manage a complex array of mail servers and third-party services like marketing automation tools. Monitor DMARC reports for any delivery issues.
From Zero to Secure: Setting Up SPF and DKIM Records
Implementing SPF and DKIM from scratch involves several critical steps:
Initial Setup:
- SPF: Identify all email senders (mail servers, ESPs) and include their IP addresses in the SPF record.
- DKIM: Generate DKIM keys and publish the public key in your domain's DNS records, ensuring alignment with the email headers.
DNS Record Management:
Regularly update the DNS records to reflect changes in your email sending infrastructure.
Utilize DNS txt record validation tools to ensure accuracy.
Ongoing Maintenance and Compliance:
Stay vigilant for any changes that require updates to SPF and DKIM records, such as adding new mail servers or changing email service providers.
Ensure compliance with best practices, keeping an eye on authentication methods and using tools like DMARC to monitor email delivery success.
Step-by-Step Guides for SPF, DKIM, and DMARC Setup
SPF Records: A Step-by-Step Setup Procedure
Setting Up SPF in Your DNS
SPF (Sender Policy Framework) records, which are essentially DNS TXT records, play a pivotal role in certifying which mail servers have the authorization to send emails on your domain's behalf. This enhances the security and reliability of your email communication.
To implement SPF records, you need to add a TXT record to your domain’s DNS settings containing the necessary SPF information.
This section guides you through the setup process for SPF across various Email Service Providers (ESPs). While we focus on GoDaddy as the domain host, the fundamental steps are similar across different providers.
We’ll start by outlining the general process applicable to most ESPs.
Here's a table showing the SPF record values for different DNS Host Providers and ESPs (Email Service Providers):
General SPF Setup
Regardless of your ESP, setting up SPF typically involves these straightforward steps:
Accessing Your Domain Account:
- Log in to where your domain is registered.
Navigating to TXT Records:
- Find the section in your account where TXT records are listed.
Checking Existing SPF Records:
- Look for any existing SPF records, identifiable by v=spf1 at the beginning.
Creating New TXT Records:
Detailed Steps
Log in to Your Domain Provider:
- Access your account and locate your hosting provider’s dashboard.
Find Your TXT Records:
- Under Domain Management or a similar page, look for the TXT records section.
Setting Up SPF for Specific ESPs and Hosts
For instance, with GoDaddy as your DNS host:
- GoDaddy DNS for SPF and DKIM:
- Verify if an SPF record exists, starting with v=spf1.
- Create a new TXT record using guidelines, like setting Name/Host/Alias to @ or blank, Time to Live (TTL) to 3600 or as default, and Value to something like v=spf1 include:_spf.google.com ~all for Google accounts.

SPF in Google Workspace
Setting up SPF for Google Workspace, particularly when using GoDaddy as your domain host, involves a few extra steps:
Access Google Workspace Admin Console:
- Navigate to the Account and Domains section to manage and add domains.
Verify and Activate Domain:
- After adding your domain, go through the verification process and set up Gmail, which includes MX record setup.
Automatic SPF Setup:
- Google Workspace typically configures SPF records automatically upon domain verification and Gmail activation.

SPF in Microsoft/Office 365 Accounts
For Microsoft 365 users:
- Adding Your Domain:
- In the Microsoft 365 admin center, add your domain and verify it through TXT records in your DNS settings.

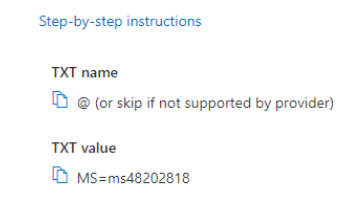
- Updating DNS Records:
- Follow Microsoft's guidance to update DNS records, including MX, CNAME, and SPF records, ensuring secure and authentic email communication.
DKIM Configuration: Detailed Implementation Guide
DKIM, the encrypted key in your email headers, is crucial for preventing email spoofing. It involves generating keys from your ESP and updating them in your domain’s DNS settings. Here's how to set up DKIM for various providers:
DKIM in Google Workspace
Google Workspace users can follow these steps for DKIM setup. Note that DKIM can only be generated after 24 hours of activating a new Google account:
- Accessing Email Authentication Settings:
- In your Google Admin console, navigate to Apps > G Suite > Settings for Gmail, and click on “Authenticate Email.”

- Selecting Your Domain:
- Choose the domain for which you're setting up DKIM. By default, it will be your primary domain, but you can select a different one if needed.
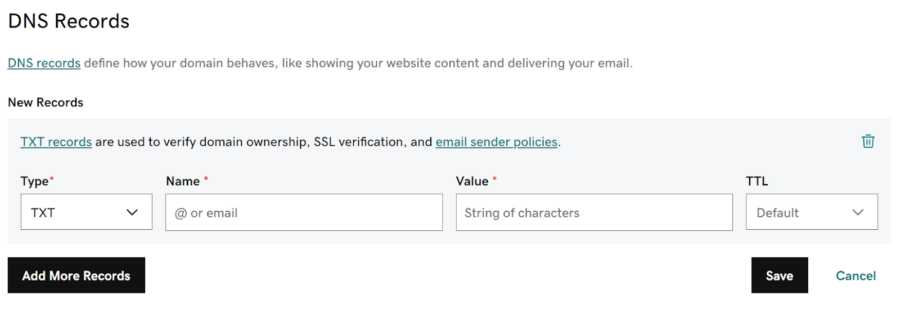
- Generating the DKIM Record:
- Generate a new record. If your registrar doesn't support 1024-bit keys, switch to 2048-bit keys for enhanced security, and then click "Generate" to obtain your public key.

- Updating DNS Provider Records:
- Log into your DNS provider's account, navigate to your domain's advanced settings, and add a new TXT record. Input the DNS hostname from Google in the “Name” field and the public key in the “Value” field.
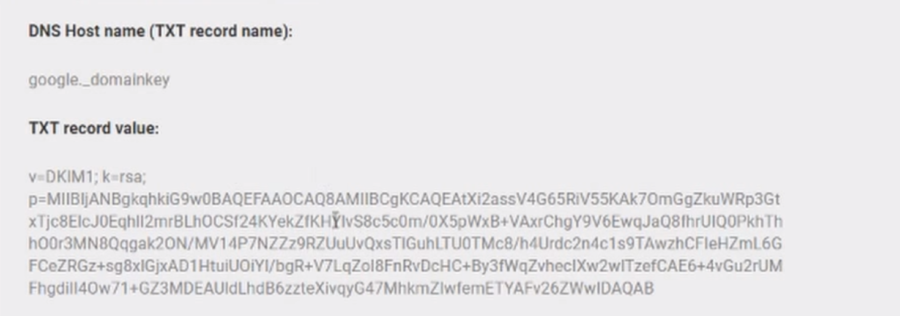

Initiating DKIM Authentication:
- Once the DNS record is added, return to the Google Admin console and select “Start Authentication.”
DKIM in Microsoft/Office 365 Accounts
For Microsoft 365 users, follow these steps:
Enabling DKIM in MS Workplace:
- Navigate to the DKIM page for your domain and select the domain you want to configure.
Activating DKIM:
- Switch DKIM to “Enable” and click on “Create DKIM keys” in the pop-up window to generate the keys.
Adding CNAME Records to DNS:
- Copy the provided CNAME-type records and add them to your DNS settings with your domain host (e.g., GoDaddy).
Updating GoDaddy DNS Records:
- Ensure that both CNAME records are updated correctly in GoDaddy's DNS settings.
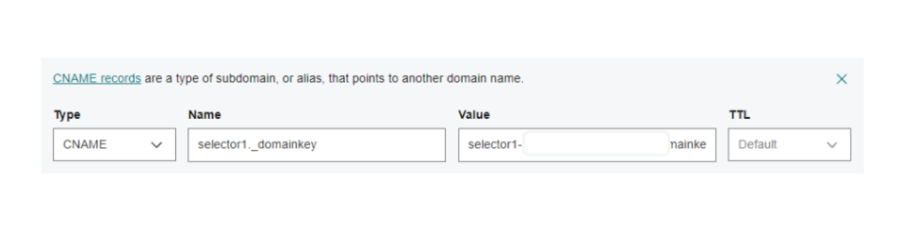
Finalizing DKIM Setup:
- Once the DNS records are updated, return to Microsoft’s DKIM page and click “Enable” to complete the setup.
DMARC Record Setup: Securing Your Email Ecosystem
Setting up a DMARC record is a crucial step in enhancing the security of your email communications, applicable across various email service providers like Outlook, Gmail, and Yahoo. Here’s a detailed guide to setting up your DMARC record:
Step 1: Registering for a DMARC Analyzer Account
- Begin by creating a free account at DMARC Analyzer, a tool available at DMARCanalyzer.com. This service offers a 14-day free trial, allowing you to monitor one domain for any signs of abuse, such as unauthorized use or reports of abuse. For instance, if you're monitoring the domain 'alore.io', DMARC Analyzer will help track any misuse of this domain in email communications.
Step 2: Utilizing the Free Account
- With your free account, you have the opportunity to closely monitor your domain. This monitoring is essential for identifying any potential abuse or unauthorized use of your domain in email communications. It's a proactive step to safeguard your domain's reputation and ensure the integrity of your email ecosystem.
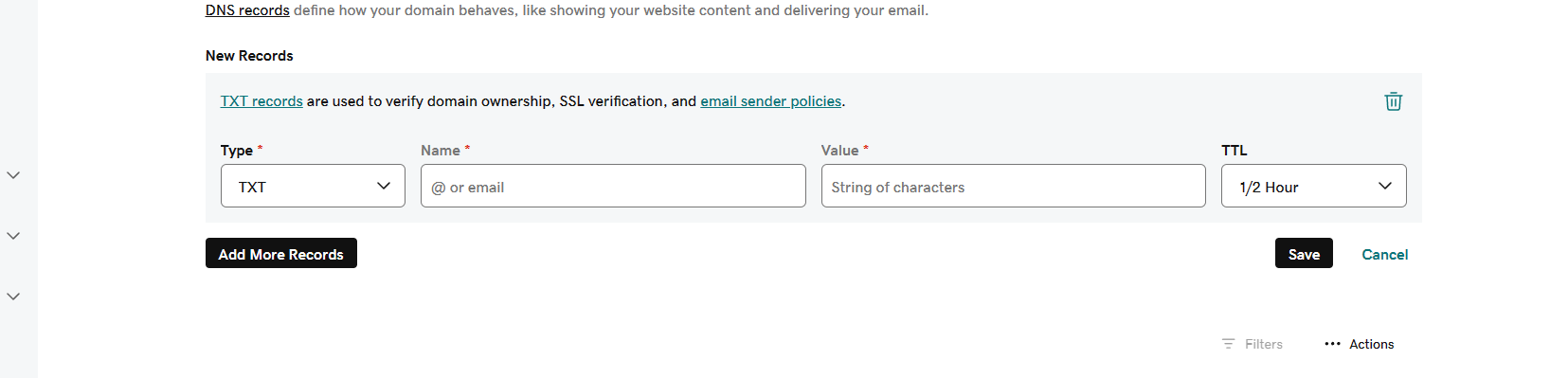
Step 3: Add TXT Record
- Go to your DNS Provider account and as the generated record as TXT record
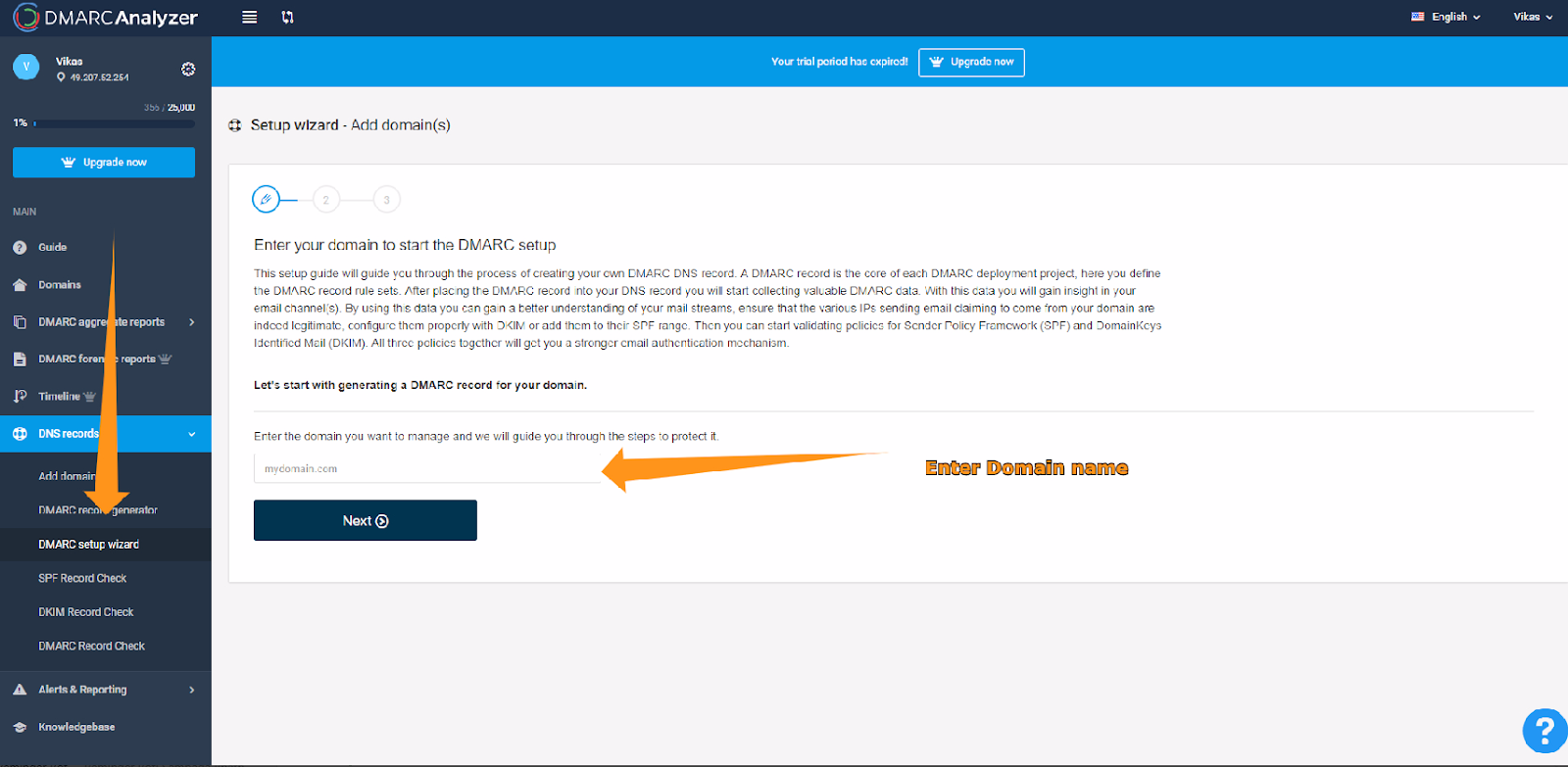
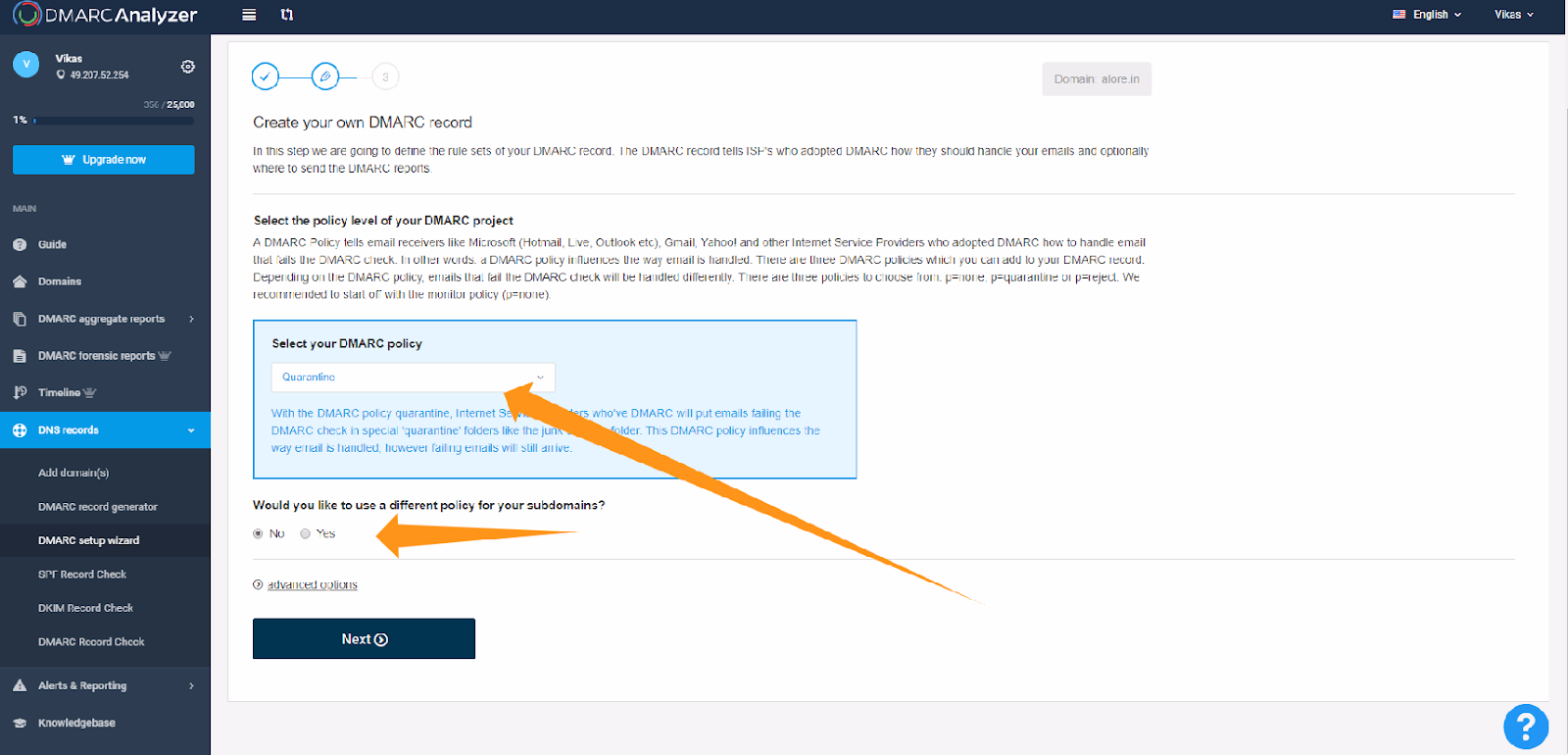

Additional Steps: Verifying Domain Health
After setting up your DMARC record, it's important to check the health and effectiveness of your email domain:
- Using MXToolbox for Domain Verification
- Visit MXToolbox, a reliable tool for checking the health of your domain.
- Enter your email domain, for example, at https://mxtoolbox.com/domain/alore.io.
- The tool will analyze your domain’s DMARC, SPF, and DKIM records.

- Interpreting MXToolbox Results
- Pay attention to any errors highlighted in red by MXToolbox. These errors are critical issues that need to be addressed to ensure your email domain's health and security.
- The goal is to resolve these issues so that all indicators turn green, signifying a healthy and secure domain.
- Updating Records and Waiting for Propagation
- Remember, changes made to your domain's DNS records, including DMARC, may not be instantaneous.
- It typically takes around 5 minutes for records to update, but it could take longer depending on your DNS provider’s update frequency.
Advanced Insights into SPF, DKIM, and DMARC
Interpreting SPF Records: A Detailed Overview
SPF (Sender Policy Framework) records are a cornerstone in email authentication, designed to prevent email spoofing and ensure sender legitimacy. Understanding and interpreting these records involves several layers:
Decoding SPF Syntax:
- SPF records, housed in DNS txt records, contain a series of directives specifying which mail servers or IP addresses are authorized to send emails on behalf of the domain.
- Key elements include mechanisms like 'include,' 'a,' 'mx,' and qualifiers such as '+all' or '-all.'
SPF Record Analysis:
- Regular analysis of SPF records is crucial to maintain email deliverability and compliance. Tools like SPF checkers can help in identifying any misconfigurations or necessary updates.
- SPF records must be carefully managed to avoid exceeding the DNS lookup limit, which can lead to SPF failures and email delivery issues.
Implications for Email Security:
A correctly configured SPF record is a strong defense against phishing attacks and unauthorized use of your domain.
Here are some examples of SPF (Sender Policy Framework) records and explanations of what they mean:
Example 1: "v=spf1 ip4:192.168.0.1 -all"
Meaning: This SPF record allows emails to be sent from the IP address 192.168.0.1. The -all at the end indicates a hard fail for any emails sent from IP addresses not listed in the SPF record, suggesting they should be rejected.
Example 2: "v=spf1 a mx include:_spf.google.com ~all"
Meaning: This record allows emails from the domain's A record (its own IP address) and its MX records (mail exchange servers). It also includes SPF records from _spf.google.com (common for domains using Google Workspace for email). The ~all signifies a soft fail for other sources, implying that emails from other sources should be treated with suspicion but not outright rejected.
Example 3: "v=spf1 +a +mx +ip4:192.168.0.1 ?all"
Meaning: Here, emails are allowed from the domain’s A record, its MX records, and a specific IP address (192.168.0.1). The + signs are explicit indicators of permission, though they are optional as this is the default behavior. ?all indicates a neutral stance on emails from other sources, neither authorizing nor rejecting them outright.
Example 4: "v=spf1 include:example.com -all"
Meaning: This SPF record allows emails from all the sources authorized by example.com's SPF record. The -all indicates that emails from any other source should be rejected.
Example 5: "v=spf1 ip4:192.168.0.1/24 ~all"
Meaning: This allows emails from any IP address within the specified IPv4 range (192.168.0.1 to 192.168.0.255). The ~all suggests a soft fail for emails from outside this range, meaning they may be marked as suspicious.
Each SPF record is tailored to the specific needs and configuration of the domain it is associated with. The selection of mechanisms and qualifiers (-all, ~all, ?all) depends on how strictly the domain wants to enforce its email-sending policy.
DKIM Records: Verification and Analysis
DKIM (DomainKeys Identified Mail) uses digital signatures to ensure the integrity and authenticity of an email. Understanding DKIM involves:
Key Generation and Management:
-Generate a pair of keys (private and public). The private key is used by the mail server to sign outgoing emails, and the public key is published in the domain's DNS records.
-Regularly rotate DKIM keys to maintain security.
Analyzing DKIM Signatures:
-Each email contains a DKIM signature in its header. This signature is verified against the public key in the sender's DNS records.
- Analyzing DKIM signatures involves checking for alignment, validity, and any tampering of the email content.
Enhancing Email Trust:
-Proper DKIM setup strengthens the domain's reputation with email providers, increasing the chances of emails being delivered successfully.
DMARC: Policies, Reporting, and Domain Owner's Role
DMARC (Domain-based Message Authentication, Reporting, and Conformance) combines SPF and DKIM, adding a policy layer:
Setting DMARC Policies:
- DMARC policies are specified in the domain's DNS settings and instruct receiving email servers on how to handle emails that fail SPF or DKIM checks.
- Policies range from 'none' (monitoring mode) to 'reject' (actively blocking failed emails).
DMARC Reporting and Analysis:
- DMARC generates reports that provide valuable insights into email delivery, highlighting any SPF or DKIM failures.
- Regular review of these reports helps domain owners identify and rectify issues affecting email security and deliverability.
The Domain Owner’s Responsibility:
- It's imperative for domain owners to actively manage DMARC, SPF, and DKIM records to protect their email communication.
- This includes regular audits, updates to DNS txt records, and staying informed about evolving email authentication protocols and standards
Here are the same DMARC record examples and their meanings:
Example DMARC Record: v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com;
Meaning:
- v=DMARC1: Indicates the DMARC version being used.
- p=none: The domain is not enforcing DMARC policy, merely monitoring. Emails failing DMARC checks will not be rejected or quarantined.
- rua=mailto:dmarc-reports@example.com: Aggregate reports on DMARC failures will be sent to this email address.
Example DMARC Record: v=DMARC1; p=quarantine; pct=100; rua=mailto:dmarc-reports@example.com;
- Meaning:
- v=DMARC1: Indicates the DMARC version being used.
- p=quarantine: Emails failing DMARC checks should be quarantined (typically moved to the spam folder).
- pct=100: This policy should be applied to 100% of the emails.
- rua=mailto:dmarc-reports@example.com: Aggregate reports to be sent to the specified email address.
Example DMARC Record: v=DMARC1; p=reject; adkim=r; aspf=r; rua=mailto:dmarc-reports@example.com;
- Meaning:
- v=DMARC1: Indicates the DMARC version being used.
- p=reject: The domain's policy is to reject emails that fail DMARC checks.
- adkim=r and aspf=r: Specifies relaxed alignment for both DKIM and SPF. This means the email's From domain must match the DKIM and SPF authenticated domains in some recognizable way but doesn't need to be an exact match.
- rua=mailto:dmarc-reports@example.com: Specifies where aggregate DMARC reports should be sent.
These examples illustrate the different approaches a domain owner can take regarding their DMARC policy, ranging from no enforcement to active rejection of emails that fail to pass DMARC verification. This flexibility allows for varying levels of security and control over email authentication and deliverability.
Tools and Methods for SPF, DKIM, and DMARC Verification
How to Check SPF and DKIM in Gmail
Verifying SPF through Email in Gmail
To ascertain if SPF is functioning correctly, a straightforward method is to inspect your emails. Here's how you can do this using Gmail:
Send a Test Email:
- Compose and send an email to your own account from the domain you're examining for SPF.
- Once received, open the email and select “Show details” to view its source. The option's name might differ based on the email client.

Examine Email Headers:
- Look for the “mailed-by” header, which should display your domain's name.
- Ensure that the “signed-by” header matches the domain from which the email was sent.
- The presence of accurate “mailed-by” and “signed-by” headers usually signifies proper SPF and DKIM configuration.

Utilizing Gmail’s 'Show Original' Feature for SPF and DKIMTo delve deeper into your email's authentication details, Gmail provides a handy tool:
Locate and Open the Email:
- Open the specific email in your Gmail account.
- Click on the vertical three dots in the top-right corner of the email window.
Access Full Email Headers:
- From the dropdown menu, select “Show original.”
- This action will open a new window or tab displaying the full email headers.
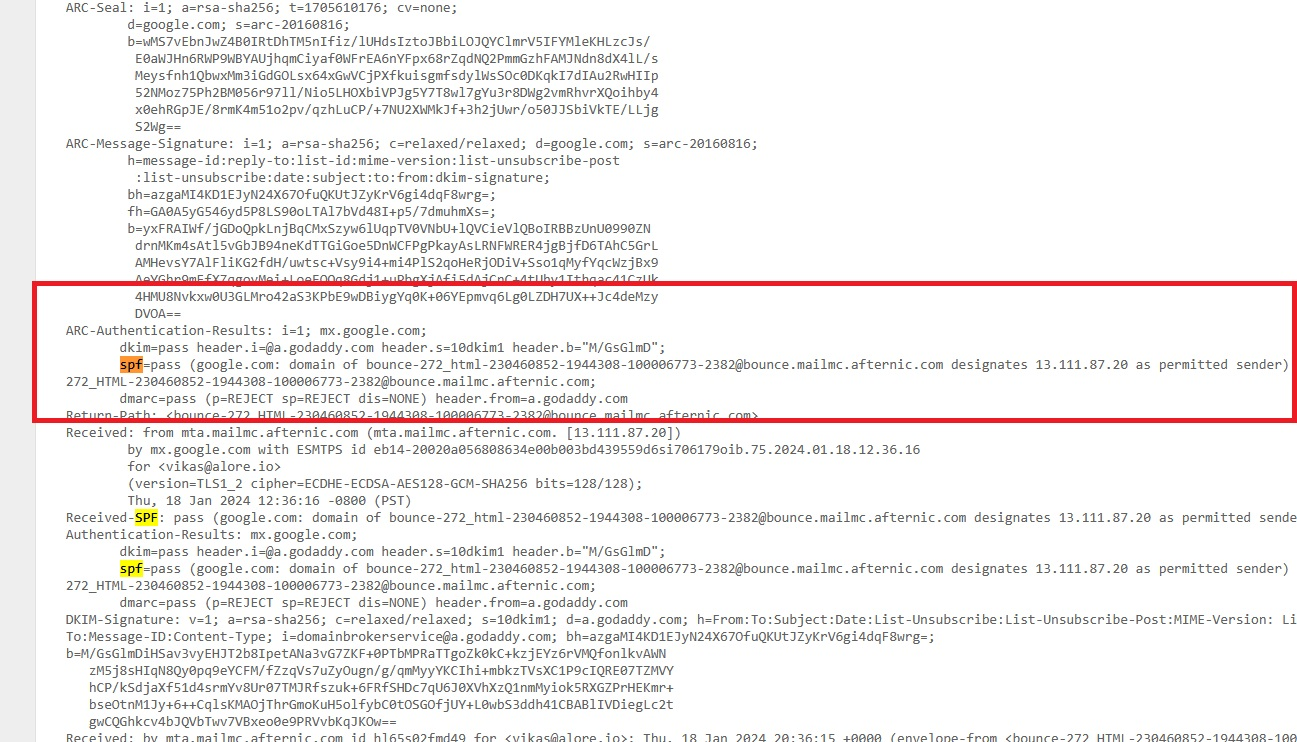
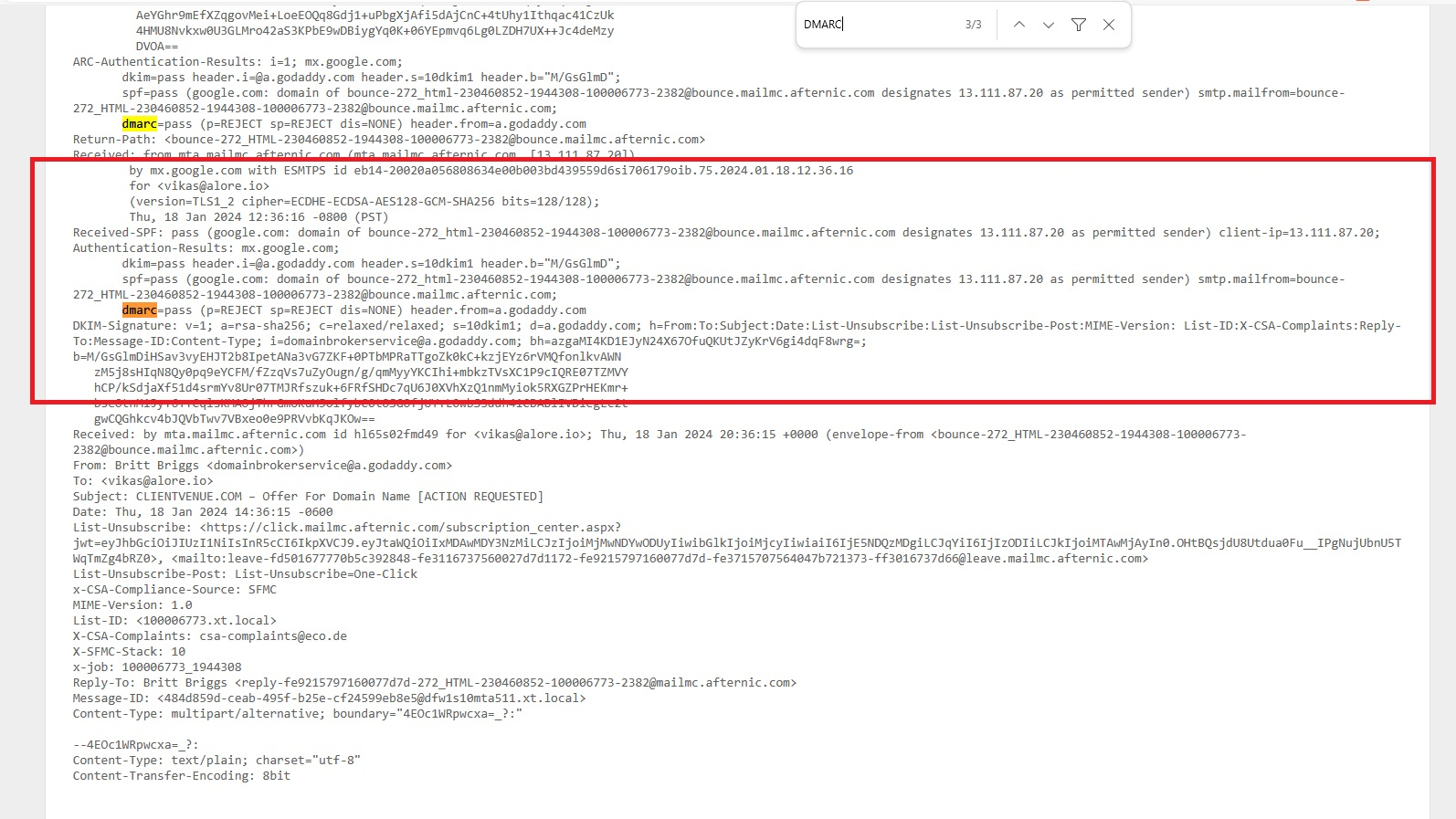
Analyze SPF, DKIM, and DMARC Details:
- Look for sections that mention SPF, DKIM, and DMARC.
- These segments will contain information about the alignment and policies of SPF, DKIM, and DMARC.
- If both your IP and domain are marked as passed, it indicates that your SPF and DKIM settings are configured accurately.

Note on SPF and DKIM Configuration in Gmail
- If you find that your SPF settings aren’t configured, don’t worry. There are straightforward steps to set them up properly.
- Be cautious not to have multiple SPF records as it might lead to authorization issues and appear suspicious.
- By correctly configuring these settings, you can ensure your emails reliably bypass spam filters.
Validating SPF Records: Essential Tools and Techniques
Verifying SPF records is vital for maintaining email security and ensuring deliverability. Here are some key tools and techniques:
- MXToolbox.com:
- MXToolbox is a popular tool for checking SPF records. It provides a comprehensive analysis of your SPF record, highlighting any configuration errors and ensuring that all mail servers are correctly authorized.
Usage: Enter your domain, and MXToolbox will display the SPF record, along with a detailed breakdown of the IP addresses and mechanisms included in it.
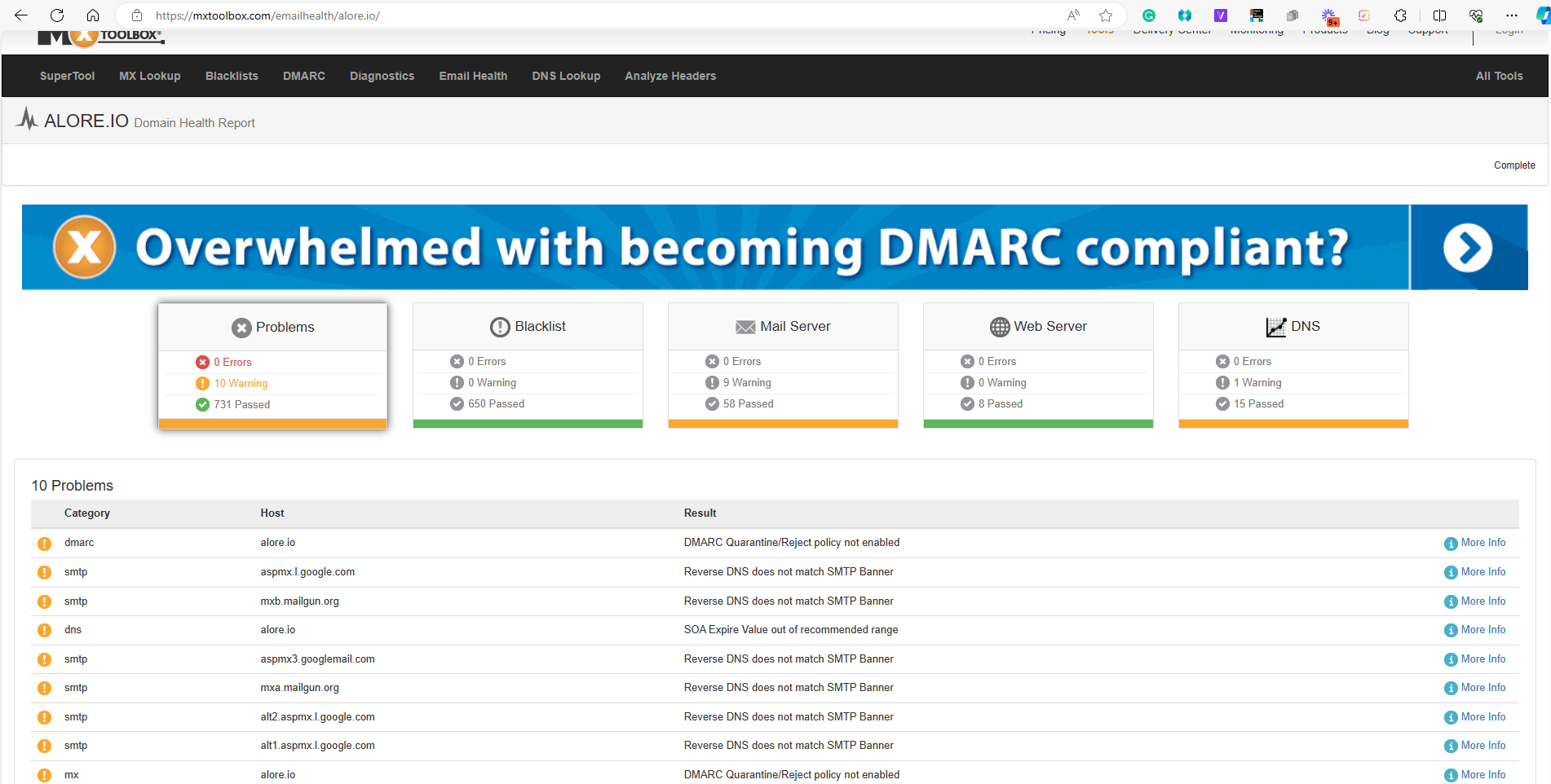
Manual Verification and DNS Checkers:
- Besides automated tools, manually examining the DNS txt records for SPF entries is crucial. Ensure that the SPF record includes all necessary mail servers and aligns with your email sending practices.
- DNSChecker.org offers a user-friendly interface to verify DNS records, including SPF. It's beneficial for confirming that your SPF record is propagated correctly across different DNS servers globally.
DKIM Verification: Tools and Command Line Methods
Ensuring the integrity of DKIM setup is essential for email authenticity:
- Online DKIM Validators:
- Tools like DKIMValidator.com help verify the DKIM signature of an email. They check if the email's DKIM signature matches the public key in the domain's DNS, indicating a valid and intact email.
- Google Admin Console can also be used for DKIM verification, especially useful for domains using Google Workspace for email services.
- Using Command Line Tools:
- Command-line tools like dig or nslookup are excellent for querying DNS records for DKIM entries. These are essential for those managing email servers directly, offering a more technical approach to verification.
DMARC Compliance: Ensuring Proper Configuration
DMARC is crucial for aligning SPF and DKIM, ensuring a robust email authentication strategy:
- Analyzing DMARC Policies and Reports:
- Tools like EasyDMARC.com provide an intuitive platform to analyze DMARC reports. These reports help in understanding how your emails are being processed and authenticated, highlighting any issues with SPF or DKIM configurations.
- Regular review of DMARC records in your DNS txt records is also necessary to ensure the policy reflects your current email security posture.
- The Role of Domain Owner in DMARC Implementation:
- As a domain owner, regularly audit and update DMARC and SPF and DKIM records. Staying informed about email authentication standards and using tools like MXToolbox, DNSChecker, and EasyDMARC will aid in maintaining a secure email environment.
Best Practices for Domain Owners in Email Authentication
Optimal Management of SPF Records: Limitations and Solutions
SPF (Sender Policy Framework) is a key tool for domain owners to authenticate their email sources. Here's how to effectively manage it:
- Understanding SPF Limitations:
- SPF can only verify the source IP of the email, not the header or content. This limitation can lead to the SPF fail issue if not properly configured.
- You can not have more than one SPF Record
- Be mindful of the DNS lookup limits (not more than 10). Exceeding this limit can result in legitimate emails being marked as spam.
- Solutions for Effective SPF Management:
- Regularly audit and update the SPF record to include all authorized sending IP addresses and email servers.
- Use DNS txt record tools like MXToolbox to check the validity of your SPF record.
Incorporating Multiple IP Addresses and ESPs in SPF
Handling multiple sending sources requires strategic SPF management:
- Consolidating Sending Sources:
- Include all IP addresses of your mail servers and any external Email Service Providers (ESPs) in your SPF record.
- Ensure that each email sender, including email servers and email senders, is authenticated through SPF.
- Regular Updates and DNS Checks:
- Update your SPF record when adding new mail servers or changing ESPs. Use tools like DNSChecker to ensure global DNS propagation.
DKIM Record Optimization: Best Practices
For DKIM (DomainKeys Identified Mail), the following practices are recommended:
- Regular Key Rotation:
- Rotate your DKIM keys periodically to maintain security. This involves updating the DKIM records in your domain's DNS settings.
- Ensure your DKIM signature aligns with your email headers to avoid authentication failures.
- Consistent DKIM Implementation:
- Apply DKIM to all outgoing email messages, including those sent from different email servers within your organization.
Strengthening Email Deliverability with DMARC
DMARC (Domain-based Message Authentication, Reporting, and Conformance) plays a pivotal role:
- Implementing a Robust DMARC Policy:
- Set up a DMARC policy that aligns with your security needs, ranging from monitoring (p=none) to enforcing (p=reject).
- Include DMARC authentication mechanisms in your DNS records to enhance email security.
- Utilizing DMARC for Feedback and Adjustment:
- Regularly review DMARC reports to understand how your emails are being processed and to identify any delivery issues.
- Use these insights to fine-tune your SPF and DKIM configurations, ensuring optimal email deliverability and domain reputation.









