Understanding DMARC Records: What is DMARC Record?
The Importance of DMARC in Email Security
DMARC (Domain-based Message Authentication, Reporting, and Conformance) records are vital for ensuring the integrity of email communications.
They enable domain owners to set policies that dictate how receiving mail servers should treat emails that don’t align with the established DMARC authentication.
This approach plays a critical role in minimizing email fraud, particularly phishing and spoofing.
Domain-Based Message Authentication: A Closer Look
Integrating DMARC with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) enhances email authentication.
SPF lists authorized mail servers for a domain, while DKIM provides a digital signature for each outgoing email from the organizational domain.
DMARC uses these technologies to verify email authenticity, instructing email receivers on handling emails that fail these checks.
DMARC Explained Simply
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. Think of it as a security guard for email messages.
Protects Your Email Domain
It helps to ensure that emails sent from your domain (like your school's email address) are genuine, legitimate messages from your domain and not fake ones sent by imposters.
Works with SPF and DKIM
DMARC teams up with two other email security methods - SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). SPF makes sure emails are sent from approved servers, and DKIM adds a digital signature to verify an email message's authenticity.
Tells Email Receivers What to Do
Setting up a DMARC record in your domain's DNS (Domain Name System, like an internet phonebook) tells email receivers how to handle emails that don’t pass SPF and DKIM checks. It’s like giving instructions on what to do with suspicious emails.
Policies for Handling Emails
DMARC lets you set policies, kind of like rules, for handling these unauthenticated spam messages and emails - either do nothing ('none'), put them in quarantine (like a waiting area for further checks), or reject them completely.
Helps Identify Email Fraud
It helps in identifying and preventing email fraud, like phishing (where someone tries to trick you into giving personal information).
Provides Reports for Monitoring
DMARC also sends back reports to the domain owner. These reports give information about which emails passed or failed the DMARC checks, offering insights for better email security.
A Tool for Better Email Security
By using DMARC, organizations can better protect their email domains from being misused for spam or phishing attacks, thus safeguarding their reputation, email message, and the security of email recipients.
How Does DMARC Work?
DMARC is designed to empower email domain owners to protect their domain from unauthorized use, often seen in email spoofing.
The effectiveness of DMARC lies in its ability to utilize and build upon the foundations laid by SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). Here's a detailed look at the functioning of DMARC:
DMARC Record Setup:
Domain owners establish a DMARC policy by publishing a DMARC record in their domain registrar or DNS (Domain Name System). This DMARC record is a TXT record that specifies the domain's DMARC policy and instructions for email receivers regarding handling emails that fail DMARC checks.
Integrating SPF and DKIM:
- SPF Verification: DMARC verifies that the sender's IP address is authorized by checking the domain's DNS records. It ensures that the email comes from a legitimate source.
- DKIM Authentication: Alongside SPF, DMARC uses DKIM, which involves attaching a digital signature to the email. This signature is then verified against a public key in the domain's DNS to confirm the email's integrity.
Alignment and Authentication:
A critical aspect of DMARC is the alignment of the domain in the 'From' address with the domains verified by SPF and DKIM. DMARC checks for either relaxed or strict alignment, adding a robust layer of email authentication.
Policy Application:
If an email fails these DMARC checks, the receiving email server then applies the action defined in the receiving mail server DMARC policy. Actions include none (taking no action), quarantine (marking the email as suspicious), or a reject mail" (blocking the email altogether).
Feedback through Reporting:
DMARC also mandates that receiving email servers send back aggregate and forensic reports to the sending domain owner. These reports provide valuable insights into the emails sent from their own domain, including those that fail DMARC authentication, enhancing overall email security.
DMARC Records: Structure and Function
Parts of a DMARC Record
DMARC records, embedded in your domain's DNS as TXT records, are composed of several parts, each serving a specific function:
Version Tag (v=): This tag signifies the version of DMARC being used, typically "DMARC1".
Policy Tag (p=): Indicates the policy for email handling (none, quarantine, reject) on DMARC failure.
Subdomain Policy (sp=): Specifies the policy for subdomains, which can be different from the main domain policy.
Percentage Tag (pct=): Defines the percentage of emails subjected to DMARC filtering.
Reporting URI for Aggregate Reports (rua=): Specifies where aggregate reports on DMARC failures should be sent.
Reporting URI for Forensic Reports (ruf=): Indicates where individual failure reports, also known as forensic reports, are sent.
DKIM Alignment Mode (adkim=): Dictates how strictly DKIM alignment should be checked (strict or relaxed).
SPF Alignment Mode (aspf=): Similar to DKIM alignment, it sets the strictness for SPF alignment.
Example of DMARC Records
Here are five examples of DMARC records, each illustrating different configurations:
Strict Policy or Restrictive DMARC Policy with Full Reporting:
- "v=DMARC1; p=reject; rua=mailto:report@example.com; ruf=mailto:forensic@example.com; pct=100"
- This record enforces a strict 'reject' policy and requests both aggregate and forensic reports for all emails.
Monitoring Mode with Aggregate Reporting:
- "v=DMARC1; p=none; rua=mailto:report@example.com"
- Here, the domain is in monitoring mode (policy 'none'), collecting aggregate reports without affecting email delivery.
Quarantine Policy for a Percentage of Emails:
- "v=DMARC1; p=quarantine; pct=50"
- This record quarantines 50% of emails that fail DMARC checks, providing a cautious approach to implementation.
Strict Policy for Subdomains:
- "v=DMARC1; p=quarantine; sp=reject; rua=mailto:report@example.com"
- While the main domain uses a 'quarantine' policy, this record specifies a stricter 'reject' policy for all subdomains.
Relaxed Alignment with Reporting:
- "v=DMARC1; p=reject; adkim=r; aspf=r; rua=mailto:report@example.com"
- This record opts for a relaxed alignment mode for both DKIM and SPF, with a strict 'reject' policy and aggregate reporting.
What are TXT Records and What's The Role of TXT Records in DMARC Implementation
Understanding TXT Records
TXT (Text) records are a type of resource record in the Domain Name System (DNS). They are primarily used to provide information to sources outside your domain.
A TXT record can hold any type of text-based data, often used for various verification methods, including security and compliance assertions in the digital realm.
- Flexible Format: TXT records can contain a variety of data formats and are not limited to any specific type of information.
- Verification and Authentication: Often used for ownership verification of a domain, email sender policy frameworks (like SPF), and other security protocols.
Role of TXT Records in DMARC Implementation
In the context of DMARC implementation, TXT records serve a critical role:
Hosting DMARC Records:
- Storage for DMARC: DMARC policies are implemented as specific TXT records in a domain’s DNS settings. This is where email servers look up the DMARC policy for a domain.
- Record Structure: A DMARC TXT record typically starts with "v=DMARC1", which identifies the version of DMARC used, followed by several tag-value pairs that dictate the DMARC policy and reporting instructions for the domain.
Enabling Email Authentication:
- Working Alongside SPF and DKIM: DMARC leverages the capabilities of SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), both of which also use TXT records in the DNS for their implementation.
- Unified Framework: While SPF and DKIM validate individual aspects of an email (like the sender's IP and message integrity), DMARC unifies these methods into a cohesive policy. It uses the results of SPF and DKIM checks to deliver a verdict on an email's authenticity.
Reporting and Compliance:
- Aggregate and Forensic Reports: DMARC TXT records can specify email addresses for sending reports on email authentication attempts (aggregate reports) and detailed forensic reports on individual failures.
- Policy Compliance: These reports are crucial for domain owners to monitor compliance with their DMARC policy and to identify and rectify authentication issues.
Enhanced Email Security:
- Preventing Domain Abuse: By implementing a DMARC policy via TXT records, organizations can significantly reduce the risk of their domains being used for email phishing or spoofing.
- Building Trust: A well-configured DMARC policy enhances the legitimacy and trustworthiness of emails originating from the domain.
Crafting and Implementing DMARC Policies
DMARC Record Implementation: A Strategic Decision
When it comes to safeguarding your email domain, implementing a DMARC record is a strategic decision that requires thoughtful consideration.
A DMARC record, essentially a TXT record in your DNS, is more than just a set of instructions; it’s a declaration of how seriously you take email security.
- Understanding the Impact: Implementing a DMARC record affects how your emails are processed globally. It's not just about preventing email spoofing; it's also about protecting your brand's reputation and the security of your email recipients.
- Considerations for Policy Setting: When configuring your DMARC policy, deciding between 'none', 'quarantine', or 'reject' requires an assessment of your organization's readiness and the potential impact on email deliverability.
How to Design Effective DMARC Policies for Domain Protection: Step by Step Guide Crafting an effective DMARC policy is essential for domain protection. Here's a step-by-step guide to help you through the process:
- Start with an Assessment: Evaluate your current email authentication practices. Ensure that your SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) records are correctly set up.
- Choose Your DMARC Policy:
- None: Use this for monitoring and collecting data without affecting email delivery.
- Quarantine: This policy will move unauthenticated emails to the spam folder.
- Reject: The strictest policy, which outright rejects unauthenticated emails.
- Implement the DMARC TXT Record: Add the DMARC record to your domain's DNS. This record should include your policy, reporting preferences (aggregate reports and forensic reports), and the email addresses where you want to receive these reports.
- Monitor and Analyze Reports: Regularly review the DMARC reports you receive. These reports are crucial for understanding how your emails are being authenticated and identifying any configuration issues.
- Adjust as Needed: Based on the insights from your reports, you may need to adjust your SPF and DKIM configurations or even update your DMARC policy to better protect your domain.
- Educate and Communicate: Ensure that your team understands the importance of DMARC. If you're setting a 'reject' policy, inform your partners and customers to expect authenticated emails only.
- Ongoing Review and Updates: DMARC is not a set-it-and-forget-it solution. Regular reviews and updates are essential to adapt to evolving email threats and maintain the integrity of your email communications.
DMARC Record Creation Questionnaire
This questionnaire is designed to guide you through the process of creating a DMARC record for your domain. By answering these questions, you'll be able to formulate a DMARC record that aligns with your email security needs and policies.
Domain Information
- What is the domain for which you are creating the DMARC record?
- Do you have subdomains that need separate DMARC policies?
Email Authentication
- Have you implemented SPF (Sender Policy Framework) for your domain?
- Have you implemented DKIM (DomainKeys Identified Mail) for your domain?
Policy Selection
- What level of DMARC policy do you wish to implement?
- None (for monitoring only, taking no action on emails that fail DMARC checks)
- Quarantine (to place unauthenticated emails in the spam/junk folder)
- Reject (to reject unauthenticated emails completely)
- For Quarantine and Reject policies, what percentage of emails would you like to apply this policy to? (1-100%)
Reporting
- Please provide an email address where aggregate DMARC reports (rua) should be sent.
- Would you like to receive forensic reports (ruf) for detailed information on individual email failures?
- If yes, please provide an email address for forensic reports.
Alignment Modes
- Choose the DKIM alignment mode:
- r for relaxed (allows partial matches between the domain in the DKIM signature and the domain in the 'From' header)
- s for strict (requires an exact match)
- Choose the SPF alignment mode:
- r for relaxed (allows partial matches between the domain in the SPF record and the domain in the 'From' header)
- s for strict (requires an exact match)
Subdomain Policy
- Do you want to specify a different policy for your subdomains?
- If yes, what policy should apply to emails from your subdomains?
Implementing DMARC: Step-by-Step Guide to DMARC Record Setup
Preliminary Steps: Ensuring SPF and DKIM are Properly Configured
Before setting up a DMARC record, it's crucial to ensure that SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) are correctly configured for your domain.
- SPF Setup: SPF authenticates the sender's IP address, preventing spoofers from sending emails on behalf of your domain. Validate your SPF record by using tools like SPF Record Check.
- DKIM Configuration: DKIM adds an encrypted signature to outgoing emails, ensuring that the content remains unaltered in transit. You can verify DKIM through your email service, as detailed in Validating DKIM records.
Verifying SPF in Gmail Emails
To check if SPF is correctly implemented, a simple technique is to examine your emails, especially in Gmail:
Sending a Test Email:
- Compose an email to your account from the domain under SPF scrutiny.
- After receiving it, open the email and click on “Show details” to inspect its source. The name of this option may vary depending on the email client you are using.
- DKIM verification is key in this process to ensure the email is sent and digitally signed by the same domain.
Analyzing Email Headers:
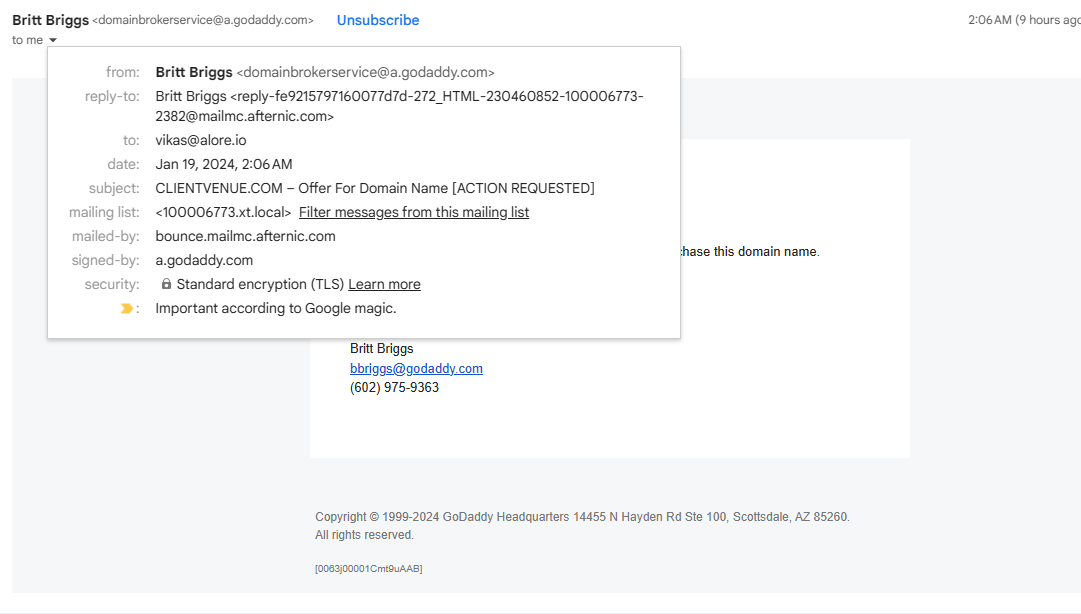
- Search for the “mailed-by” header, which should show your domain's name.
- Verify that the “signed-by” header aligns with the sending domain.
- Correct “mailed-by” and “signed-by” headers are indicative of well-configured SPF and DKIM.
Using Gmail’s 'Show Original' for SPF and DKIM Verification:
Accessing the Email:
- Open the email in your Gmail.
- Click on the three vertical dots in the email’s top-right corner.

Viewing Full Email Headers:
- Choose “Show original” from the dropdown.
- This will present the complete email headers in a new window or tab.
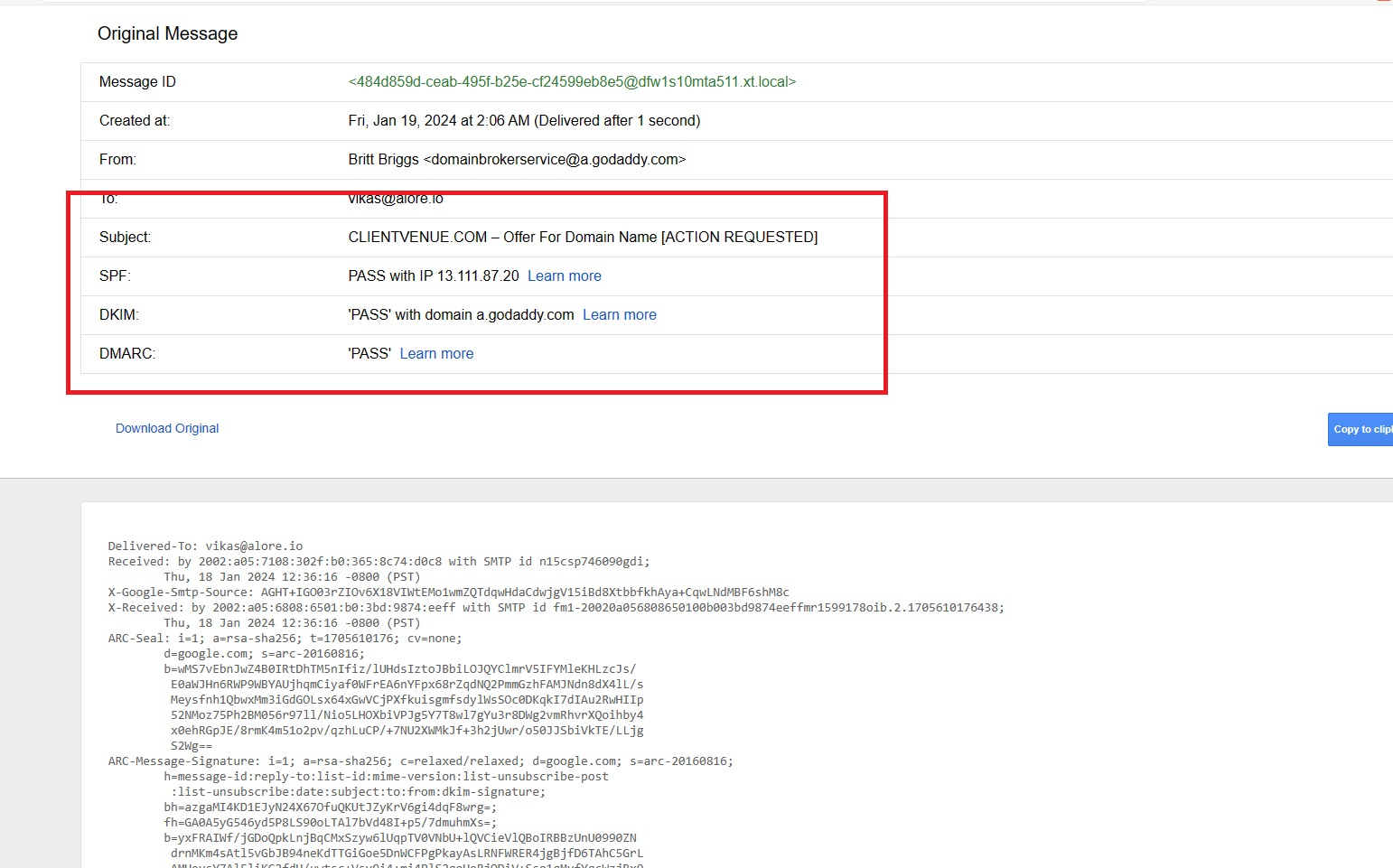
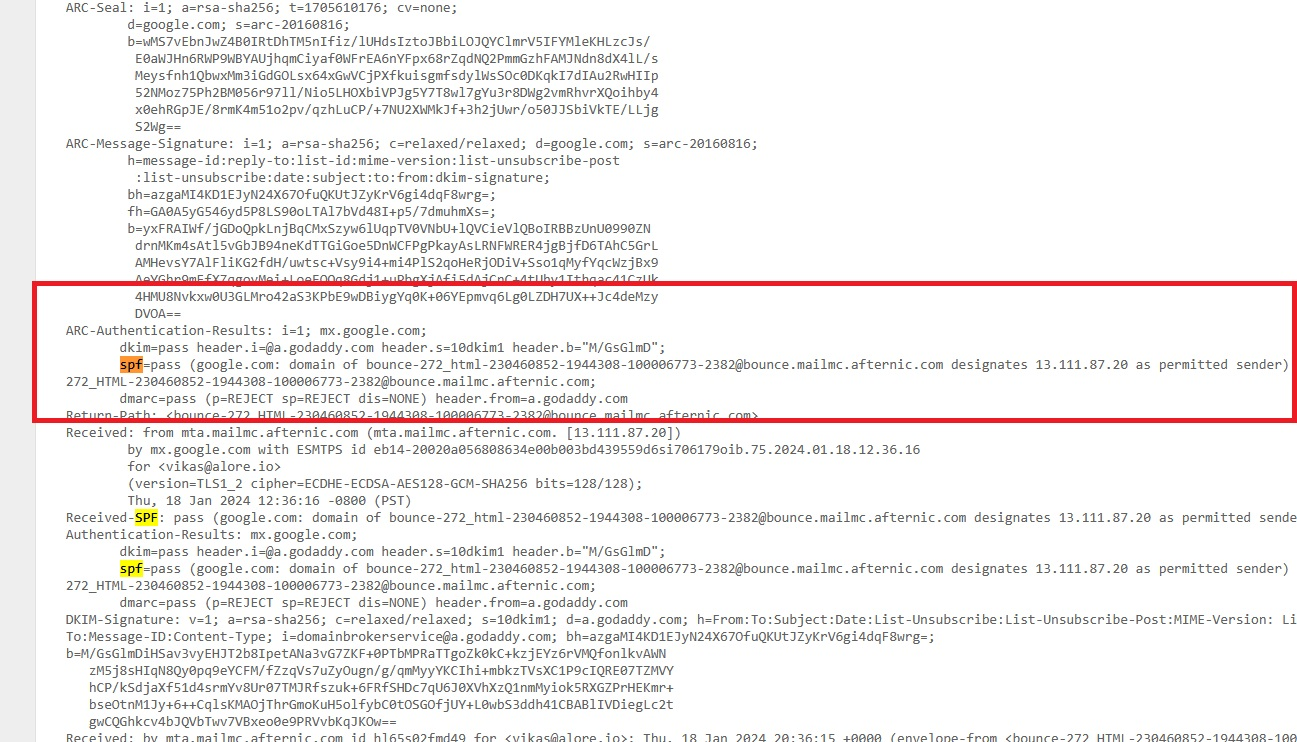
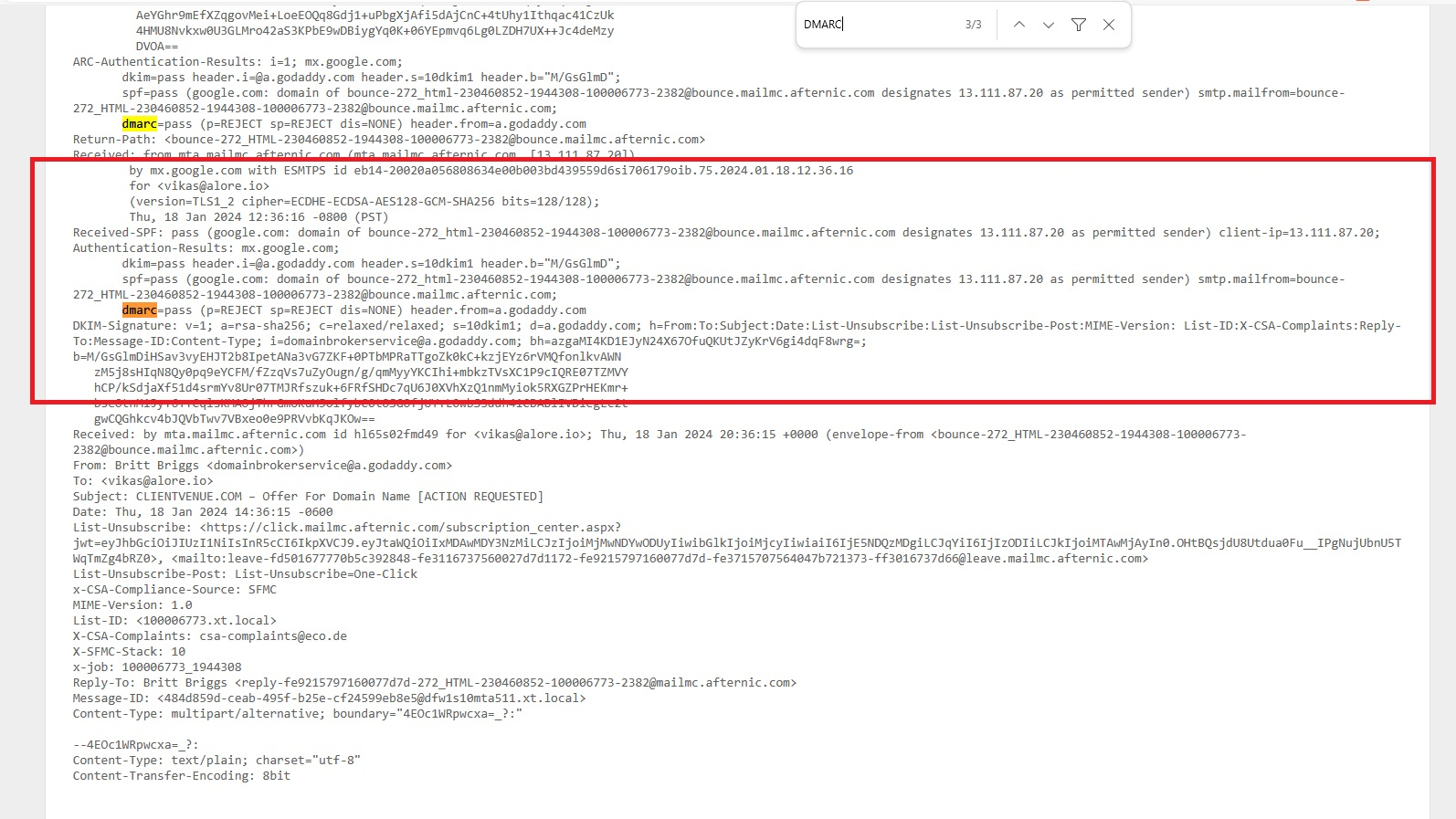
Evaluating SPF, DKIM, and DMARC:
- Look for sections mentioning SPF, DKIM, and DMARC.
- These parts will offer insights into the alignment and policies of SPF, DKIM, and DMARC.
- A 'pass' status for both your IP and domain suggests correct SPF and DKIM configuration.

Guidance on SPF and DKIM in Gmail:
- If SPF isn’t set up yet, there are easy steps for proper configuration.
- Avoid multiple SPF records to prevent authorization problems.
- Properly set SPF and DKIM help your emails consistently avoid being marked as spam.
Other Tools and Techniques for Validating SPF Records:
MXToolbox.com for SPF Checks:
- MXToolbox is a renowned SPF record analysis tool that identifies misconfigurations and verifies mail server authorizations.
- Enter your domain on MXToolbox, and it will show your SPF record with a detailed analysis of included IP addresses and mechanisms.
After running these checks, all the results are available for your analysis and further action. Detailed instructions to set, In case SPF and DKIM are not set up, detailed instructions can be found at this link.
Generating and Implementing a DMARC TXT Record
Creating and implementing a DMARC TXT record is the next step in securing your email ecosystem.
- Record Generation: Use a DMARC record generator tool to create a DMARC TXT record. Ensure it includes your policy preferences and reporting email addresses for aggregate and forensic reports. A guide for this can be found at DMARC Record Setup.
- Add DMARC record Manually to DNS: Once you have the DMARC record, add it to your domain's DNS records as a TXT record. This might involve navigating your domain registrar's or DNS provider's dashboard.
Step 1: Sign Up for a DMARC Analyzer Service
Start by signing up for a complimentary account at DMARC Analyzer, accessible at DMARCanalyzer.com. This platform offers a 14-day trial at no cost, which permits you to keep an eye on one domain for any signs of misuse, like unauthorized access or abuse complaints. For example, when overseeing the domain 'alore.io', DMARC Analyzer will assist in detecting any unauthorized or inappropriate use of this domain in email exchanges.
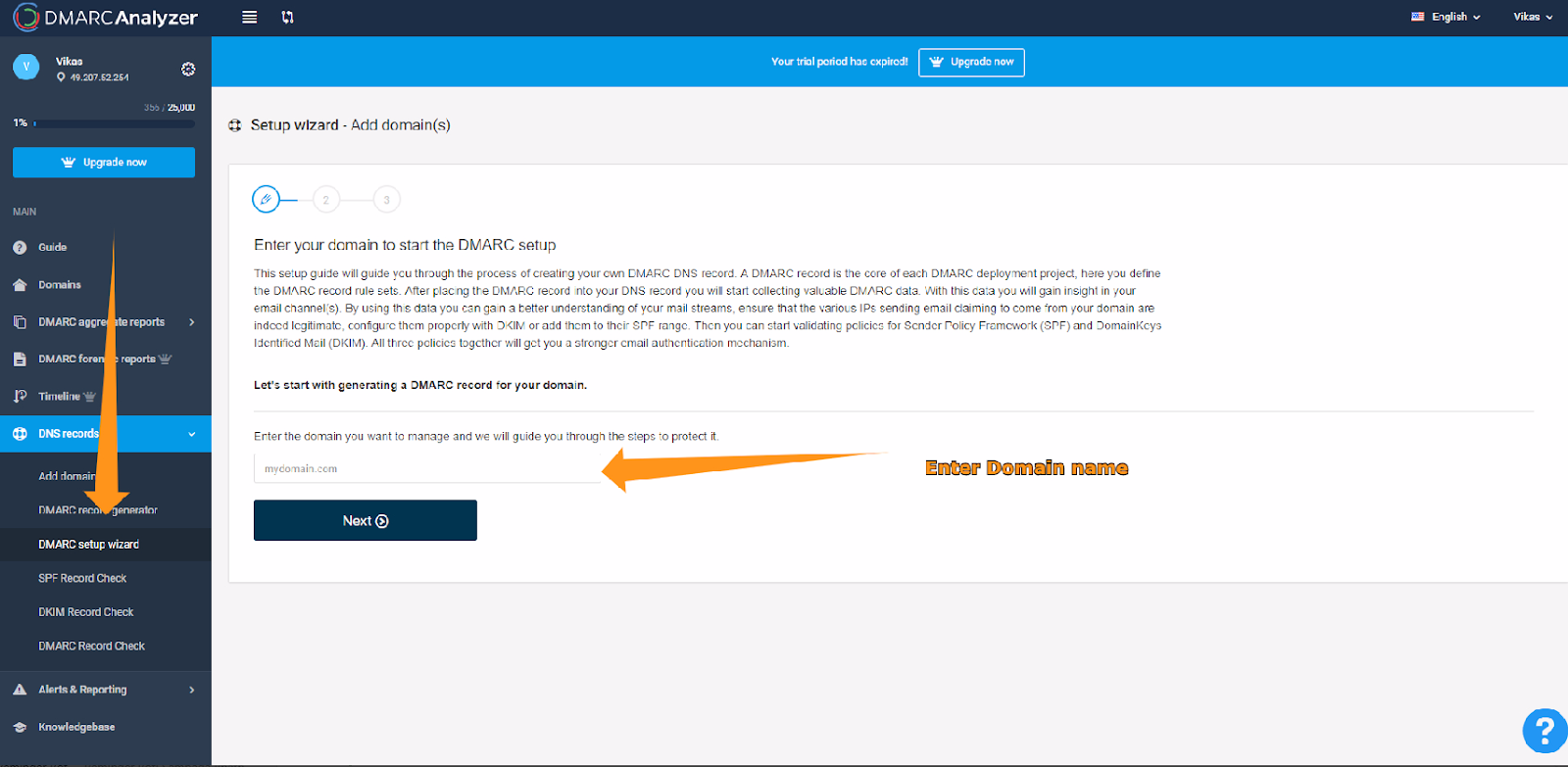
Step 2: Making Use of the Complimentary Account
Once you've set up your free account, it provides the capability to oversee your domain rigorously. This vigilance is crucial for spotting any potential misuse or unauthorized employment of your domain in email exchanges. It's a proactive approach to protect your domain's credibility and maintain your email environment's integrity.
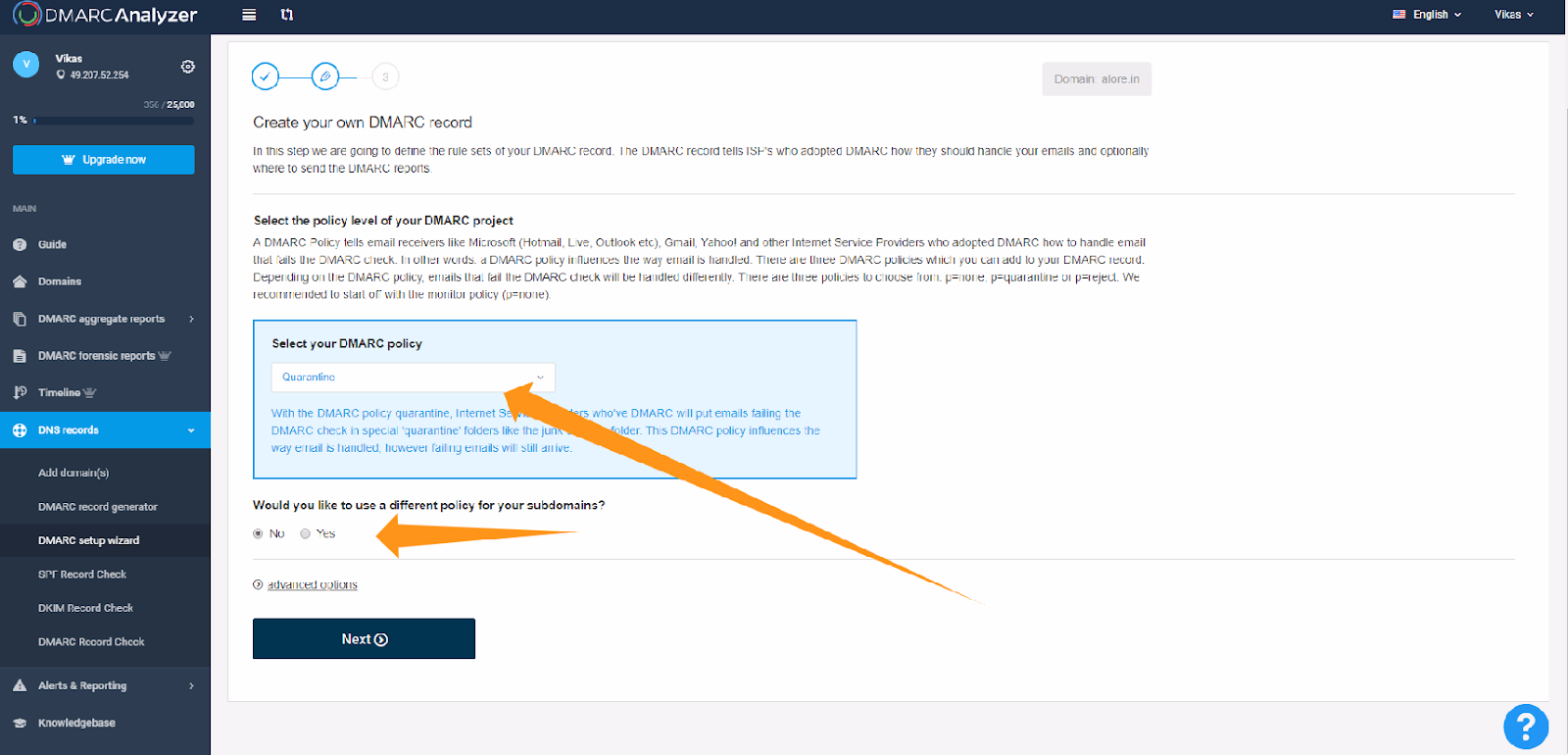

Step 3: Implementing the TXT Record
Navigate to your DNS Provider's account and insert the provided record as a TXT record.
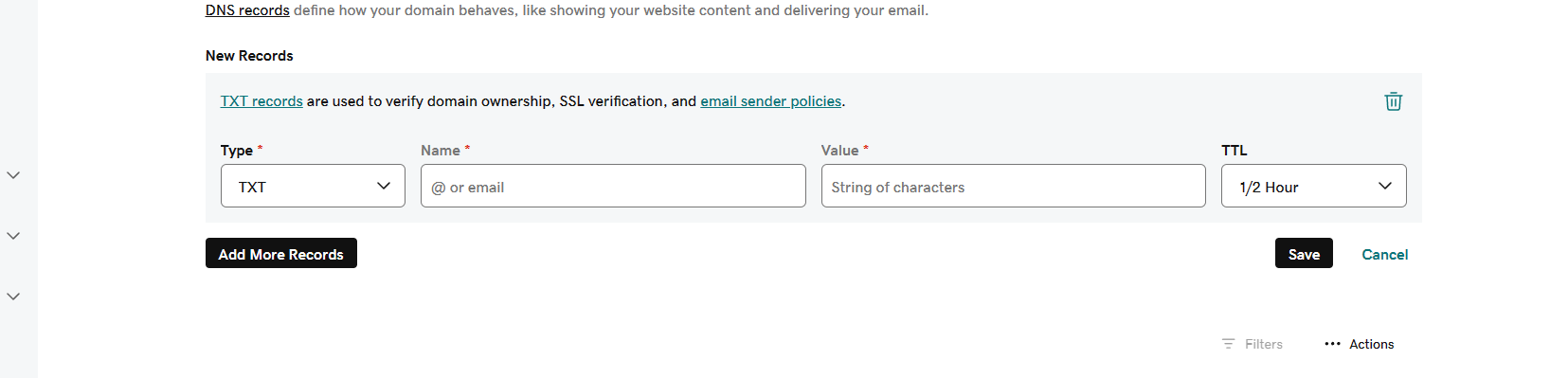
Analyzing DMARC Reports for Enhanced Security
Example of DMARC Report
An effective way to understand DMARC reports is by examining a practical example:
Sample Aggregate Report: This report, often in XML format, shows detailed records for each email sent from your domain, indicating whether each message passed or failed DMARC checks.
It will include SPF and DKIM alignment results, vital for email security, and actions taken based on your DMARC policy (none, quarantine, reject).

Interpreting DMARC Reports: A Comprehensive Overview

Deciphering DMARC reports can significantly enhance your domain's email security.
Types of Reports: Aggregate (rua) reports give an overview of all emails, while forensic (ruf) reports offer detailed insights into specific failures.
Analyzing Key Elements: Look for metrics like 'source IP', 'SPF alignment', and 'DKIM alignment' to understand the origin and authenticity of email messages.
The 'DMARC disposition' reveals how email failing checks were handled, which is crucial for assessing the effectiveness of your DMARC policy.
Spotting Trends: Identifying patterns in pass/fail rates helps in fine-tuning SPF and DKIM records, a critical step in DMARC implementation to ensure legitimate emails from your sending domain aren't wrongly flagged.
How to Utilize DMARC Reports to Fortify Email Security
Effectively using DMARC report data can strengthen your email domain's security posture.
Addressing Authentication Issues: Use insights from DMARC reports to address common failure points, like updating SPF records or correcting DKIM signatures.
This includes managing third-party senders and ensuring they comply with your email domain's security standards.
Policy Optimization: Based on the report analysis, consider adjusting your DMARC policy for better protection. This might mean transitioning from a 'quarantine' to a 'reject' policy to reduce further the chance of 'fail dmarc' incidents.
Ongoing Vigilance: Regular monitoring of DMARC reports is key in adapting to emerging email threats. Continuous analysis helps in maintaining robust email security and safeguarding your domain against spoofing and phishing attempts.
Advanced DMARC Strategies
DMARC Domain Alignment: Securing Your Email Channels
Properly aligning DMARC within your domain is essential for maintaining robust email security. Domain alignment in DMARC ensures that the domain in the 'From' header matches the domain used in SPF and DKIM records, solidifying the authenticity of the email.
- Relaxed vs. Strict Alignment: You can choose between 'relaxed' or 'strict' alignment. Relaxed alignment allows partial matches, making it more forgiving, while strict alignment requires an exact match, offering a higher security level.
- Challenges: Finding the right balance in alignment settings to avoid legitimate emails being flagged as spam.
- Solutions: Start with relaxed alignment to minimize disruption to legitimate emails (email messages from your domain), and gradually move to strict alignment as you monitor the impact.
Managing DMARC Across Subdomains: Challenges and Solutions
Implementing DMARC across subdomains can be challenging but is crucial for comprehensive domain protection. Subdomains often have different email-sending practices, which need to be considered when setting DMARC policies.
- Individual vs. Overall Policy: Decide whether each subdomain should have its own DMARC policy or inherit the main domain’s policy (domain pass dmarc). This is crucial for organizations with diverse email-sending practices across different departments.
- Monitoring and Adaptation: Regularly review DMARC reports (DMARC reporting) for each subdomain. Adjust policies based on these insights to improve email deliverability and security.
- Integration with Third-Party Services: Often, subdomains utilize third-party services for email sending (third-party service). Ensure these services align with your DMARC policy to prevent legitimate emails from being marked as fraudulent.
Comparing DMARC with SPF and DKIM: A Detailed Analysis
Email security is critical, where DMARC, SPF (Sender Policy Framework), and DKIM (DomainKeys Identified Mail) are key players. Understanding their distinct roles and how they complement each other is essential for a fortified email defense system.
DMARC: The Policy Enforcer in Email Authentication DMARC (Domain-based Message Authentication, Reporting, and Conformance) enhances the capabilities of SPF and DKIM by allowing domain owners to define how an email should be handled if it fails SPF or DKIM assessments. Key aspects of DMARC include:
- Policy Setting (DMARCpolicies): DMARC empowers domain owners to establish policies like 'none', 'quarantine', or 'reject' (v dmarc1 p reject), guiding how receivers should treat unauthenticated emails.
- Insightful Reporting (DMARC reporting): Domain owners receive crucial feedback through DMARC reports, detailing the emails passing or failing DMARC checks, thus providing visibility into email security status.
SPF: The Bedrock of Email Sender Verification SPF is a protocol to validate the sender's identity, helping combat spam and phishing. It operates by:
- IP Address Verification: SPF confirms whether the sending server’s IP is authorized in the domain’s DNS records (DNS txt record), playing a crucial role in sender verification.
- Spoofing Prevention: SPF is instrumental in identifying and blocking emails from unauthorized sources, bolstering email security.
DKIM: Upholder of Email Content Integrity DKIM provides a layer of security by attaching a digital signature to each email. It ensures:
- Content Verification: The DKIM signature validates that the email content remains unchanged during transit.
- Authenticating Sender’s Domain: By verifying the digital signature, DKIM confirms the email's origin (sender's domain).
Synergistic Relationships Among DMARC, SPF, and DKIM DMARC, SPF, and DKIM collectively enhance email security. This synergy is achieved by:
- Unified Verification Approach: DMARC leverages SPF and DKIM for a robust authentication process.
- Comprehensive Reporting and Control: DMARC's capability to generate detailed reports (DMARC report) provides domain owners with actionable insights into email traffic and potential security threats.
Implementing DMARC Records (DMARC txt record) Setting up DMARC involves creating a DMARC TXT record in your DNS. This record outlines the DMARC policy and reporting instructions, which are crucial for maintaining domain reputation and preventing email abuse.
Regular Checks and Updates for Your DMARC Record
Maintaining the effectiveness of your DMARC record is an ongoing process that requires regular checks and updates. Staying vigilant and proactive in this regard ensures your email security strategy remains robust and adaptive to new challenges.
Why Regular Monitoring is Essential
- Dynamic Email Ecosystem: The email environment is constantly evolving. New sending sources might be added, or changes in email flow could occur.
- Emerging Threats: Cyber threats are ever-changing. Regularly reviewing your DMARC setup helps you stay ahead of potential vulnerabilities.
Conducting Regular DMARC Record Reviews
- Analyzing DMARC Reports (DMARC reporting): Regularly analyze the aggregate and forensic reports from your DMARC record. These reports provide insights into the performance of your email authentication processes.
- Identifying Anomalies: Look for unusual patterns in the reports, like spikes in fail rates or sources of email that weren't previously authorized.
Updating the DMARC Record
- Adjusting to Changes: Modify your DMARC policy in response to changes in your email sending practices. For instance, if you've started using a new third-party service for sending emails, ensure it's reflected in your DMARC record.
- Enhancing Security: Gradually move towards a more restrictive DMARC policy (e.g., from 'p=none' to 'p=reject') as you gain confidence in your SPF and DKIM configurations.
Utilizing DMARC Management Tools
- Automated Tools and Services: Consider using DMARC management tools that can automate much of the monitoring and reporting process. These tools can alert you to potential issues or changes that require your attention.
- Expert Consultation: If you're not entirely confident in managing DMARC records, seeking assistance from cybersecurity experts or specialized services can be beneficial.
Periodic DNS Record Verification
- Checking DNS TXT Record (DNS txt record): Regularly verify that your DMARC TXT record in your DNS is correctly configured and hasn't been tampered with.
- Staying Compliant with Email Security Standards: Ensure your DMARC, SPF (sender policy framework), and DKIM (domainkeys identified mail) standards are up-to-date with the latest best practices and recommendations.
Conclusion
A DMARC record is not a set-it-and-forget-it tool. It demands continuous attention and adjustments to remain effective. By conducting regular checks and updates, you safeguard your domain from misuse and enhance the overall trustworthiness of your email communications.








